Web fundamentals (using burpsuit and curl) - TryHackMe!
Task 1,2,3,4
You can read their document carefully and find the answers. You can find two answers by given link on firefox HTTP format page.
Task 5 (Mini CTF)
Here I will show two methods. Watch my video for visual understanding https://youtu.be/6j4Ghryj0mY
Here is the webpage you getting :
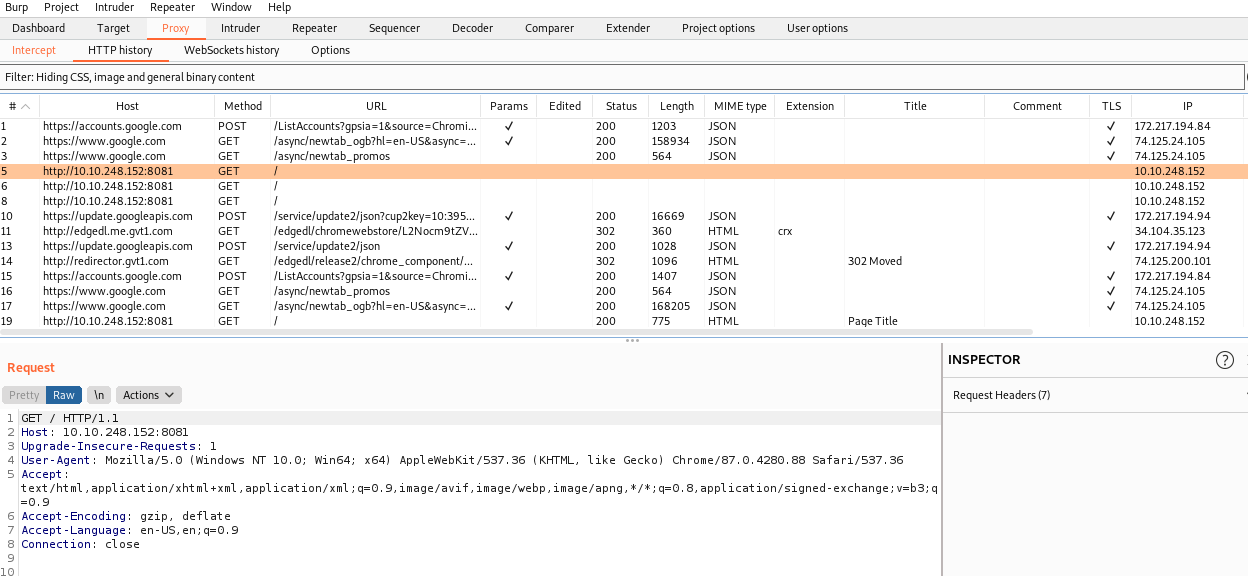
Burpsuite option
Go to the burpsuit and lunch browser then type your machine ip with the port. http://10.10.248.152:8081 this was my IP yours must be changed.
- select the right HTTP request and press CTRL+R to go to the repeater. Then type your first clue and send it.
- Then type your second clue after changing the GET to POST request. Then go to the action tab and select url encode as you type and send it.
- Now we need to get cookie. change first line to the ‘GET /ctf/getcookie’ and send it.
- Now we need to send cookie. for that we need to change the request to ‘GET /ctf/sendcookie’ and go to the inspector tab and add a cookie.
CURL option (TryHackMe method)
- GET request. /ctf/get
┌──(kali㉿kali)-[~]
└─$ curl http://10.10.248.152:8081/ctf/get
thm{flag}
- POST request. /ctf/post
┌──(kali㉿kali)-[~]
└─$ curl http://10.10.248.152:8081/ctf/post -X POST --data "flag_please"
thm{flag}
- Get a cookie. /ctf/getcookie
┌──(kali㉿kali)-[~]
└─$ curl -c - 'http://10.10.248.152:8081/ctf/getcookie'
Check your cookies!# Netscape HTTP Cookie File
# https://curl.se/docs/http-cookies.html
# This file was generated by libcurl! Edit at your own risk.
10.10.248.152 FALSE / FALSE 0 flag thm{flag}
- Set a cookie. /ctf/sendcookie
┌──(kali㉿kali)-[~]
└─$ curl -v --cookie 'flagpls=flagpls' http://10.10.248.152:8081/ctf/sendcookie
* Trying 10.10.248.152:8081...
* Connected to 10.10.248.152 (10.10.248.152) port 8081 (#0)
> GET /ctf/sendcookie HTTP/1.1
> Host: 10.10.248.152:8081
> User-Agent: curl/7.74.0
> Accept: */*
> Cookie: flagpls=flagpls
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200 OK
< Date: Tue, 18 May 2021 04:43:04 GMT
< Content-Length: 37
< Content-Type: text/plain; charset=utf-8
<
* Connection #0 to host 10.10.248.152 left intact
thm{flag}
Little secret
You can use mozila firefox to get flag
example : http://10.10.248.152:8081/ctf/get
This method you can use to ‘GET’ request …